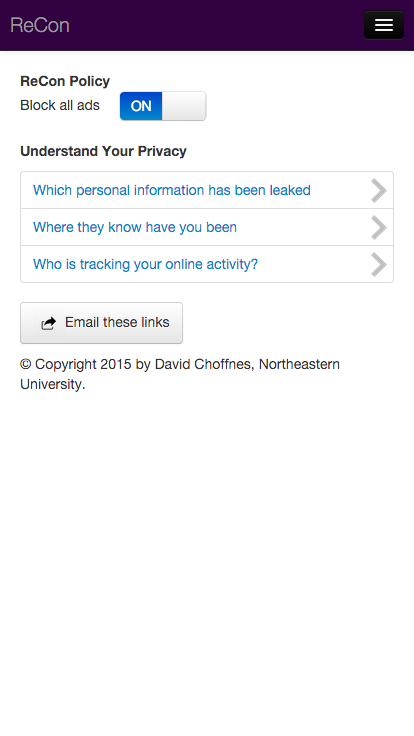
Configuration Page
Visit the configuration page from your device while connected to ReCon to access the dashboard where you can view PII leaks and configure blocking/modificaiton of PII leaks.
We will cover each component of the dashboard in subsequent slides.
If you want to view/configure ReCon services from a laptop or desktop, tap the button to send an e-mail with a link to the site.
Which PII has been leaked?
The more you use ReCon, the more PII leaks it will detect. ReCon groups PII leaks into different categories to make it easier to view.
PII is personally identifiable information (listed the red box). These include names, e-mail addresses, gender, location, device identifiers, usernames, and passwords.
Tap on a category to view detailed information about where your PII is sent, and which app is leaking it.
User feedback
By telling us whether ReCon correctly identified PII, you will help us more reliably detect future leaks.
Control your PII leaks
This feature allows you to regain control over your personal information -- you can tell ReCon to block or modify the leaks that you do not want to be sent. You can set these policies for a single PII leak, for all traffic to trackers, or for all traffic.
Once you set a policy, ReCon will apply it to future leaks matching the policy. If you install the optional ReCon companion app, ReCon will also send you notifications when it blocks or modifies leaks.
How are your locations being leaked?
We present a map view of yoru location leaks to make it easier for you to see how you are being tracked over space and time. Tap each pin to see who is tracking your location, and when they did it.